This is one of these cases when you wonder why this isn’t there by default in all Linux-based systems. In many cases, it can be useful to look at the list of the command line commands that were used on a server, and perhaps look at the user accounts that were used to issue these commands. This could help accelerate forensic investigations and incident response. It could also help in identifying the scope of a breach.
In this short tutorial, we will use syslog services to capture all commands issued in the command line, the time of command issuance, the username of the account used, and if the command was issued using SSH, we will also capture the IP address that was used in this SSH session.
Step 1: Creating the log settings file, to tell the server where to store the log entries
Create a file named /etc/rsyslog.d/commands.confusing an editor of your choice, such as nano:
sudo nano /etc/rsyslog.d/commands.conf
Add the following two lines to the new empty file:
# Log every command executed by a user to a separate file local6.* /var/log/commands.log
Save the file and exit. This will create a logger that would capture whatever you pass to local6 events and put it in the commands.log file.
Step 2: Configure your Bash shell to pass the information to the logger.
Edit your /etc/bash.bashrcfile to add these two lines:
# Set PROMPT_COMMAND to log every command to syslog PROMPT_COMMAND='history -a >(logger -p local6.debug -t "[$USER] $SSH_CONNECTION")' HISTCONTROL=null
The first command will tell bash to pass the required information to the logger called local6. The second command will tell the bash shell to capture all commands, including ones with spaces before them.
If you use other types of shell, such as zsh, or sh, make sure that you add the same two lines to their settings files to ensure that the log catches all commands used on all of these shells.
Step 3: Restarting services.
Restart syslog service:
sudo systemctl restart rsyslog
Close all open bash shell sessions, and start a new one. All of the commands types now will be captured in /var/log/commands.log file.
Example:
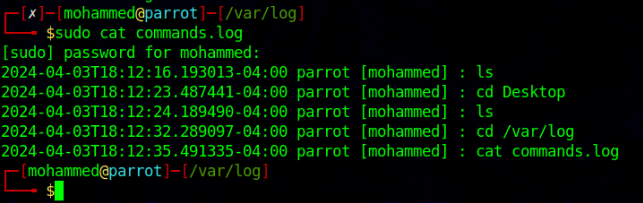
Note: You might face a scenario where “logger” command needs to run with sudo to be able to capture the passed data.